Attack Microchip PIC MCU PIC12F629
The Microchip PIC12F629 is a compact yet powerful 8-bit microcontroller (MCU) widely used in small-scale control systems, consumer electronics, and automation devices. Its low cost, internal oscillator, and high-performance flash memory make it ideal for space-constrained embedded designs. However, one of its most notable features is its strong code protection capability. This includes fuse bits that enforce readout protection, making the process to attack Microchip PIC MCU PIC12F629 extremely challenging for those seeking to recover or extract the internal firmware.

Po ustawieniu zabezpieczonego bezpiecznika kodu MCU PIC12F629, wewnętrzna pamięć programu, EEPROM i inne archiwa danych stają się niedostępne za pomocą konwencjonalnych środków. Taka konstrukcja zapewnia, że zastrzeżony kod źródłowy, pliki heksametalogowe i binarne aplikacje nie mogą być odczytane, skopiowane ani zduplikowane bez odpowiedniego dostępu. Chroni ona własność intelektualną programistów, ale również wprowadza trudności w uzasadnionych scenariuszach, w których konieczne jest odzyskiwanie oprogramowania układowego ochronnego mikrokontrolera PIC12F629 lub przywracanie urządzenia. Te chronione, szyfrowane lub zablokowane ustawienia utrudniają otwieranie, odszyfrowywanie lub pobieranie przydatnych informacji z zaszyfrowanego mikroprocesora PIC12F629 przy użyciu standardowych narzędzi. Nawet zaawansowane interfejsy debugowania są wyłączone, pozostawiając niewiele opcji dla tych, którzy próbują przywrócić lub sklonować zablokowany mikrokomputer PIC12F629 bez oryginalnych plików.
Once the code protection fuse is set, the internal program memory, EEPROM, and other data archives become inaccessible through conventional means. This design ensures that the proprietary source code, heximal files, and application binary cannot be read, copied, or duplicated without proper access. It protects developers’ intellectual property, but also introduces difficulties in legitimate scenarios where firmware recovery or device restoration is necessary.
These protected, encrypted, or locked settings make it difficult to open, decrypt, or retrieve useful information using standard tools. Even advanced debugging interfaces are disabled, leaving few options for those attempting to restore or clone a device without original files.
To attack Microchip PIC MCU PIC12F629 means to overcome the fuse bit that activates the device’s internal security. The goal is to remove or neutralize the fuse protection so the firmware can be dumped, the data extracted, and the MCU cloned or replicated onto another chip. This challenge includes several hurdles:
-
Code Security Enforcement: The device is designed to automatically erase its memory if tampering is detected.
-
Physical Microarchitecture: The internal structure of the chip is not openly documented, complicating any reverse engineering attempt.
-
Custom Protocols: The programming and memory access pathways are based on proprietary signaling, which must be decoded or mimicked for successful readout.
Even when a partial dump is possible, reconstructing the full program file accurately requires specialized knowledge of the microprocessor’s memory layout and instruction set.
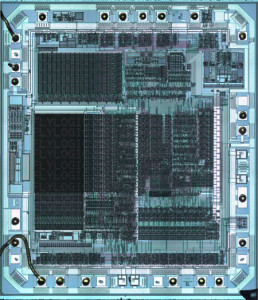
Attack Microchip PIC MCU PIC12F629
We can Attack Microchip PIC MCU PIC12F629, please find below chip features for your reference:
High-Performance RISC CPU:
· Only 35 Instructions to Learn
– All single-cycle instructions except branches
· Operating Speed:
– DC – 20 MHz oscillator/clock input
– DC – 200 ns instruction cycle
· Interrupt Capability
· 8-Level Deep Hardware Stack
· Direct, Indirect, and Relative Addressing modes
Special Microcontroller Features:
· Internal and External Oscillator Options
– Precision Internal 4 MHz oscillator factory calibrated to ±1%
– External Oscillator support for crystals and resonators
– 5 ms wake-up from Sleep, 3.0V, typical
· Power-Saving Sleep mode
· Wide Operating Voltage Range – 2.0V to 5.5V
· Industrial and Extended Temperature Range
· Low-Power Power-on Reset (POR)
· Power-up Timer (PWRT) and Oscillator Start-up Timer (OST)
· Brown-out Detect (BOD)

Uma vez acionado o fusível de proteção do código MCU PIC12F629, a memória interna do programa, a EEPROM e outros arquivos de dados tornam-se inacessíveis por meios convencionais. Este projeto garante que o código-fonte proprietário, os arquivos hexadecimais e o binário do aplicativo não possam ser lidos, copiados ou duplicados sem o devido acesso. Ele protege a propriedade intelectual dos desenvolvedores, mas também apresenta dificuldades em cenários legítimos onde a recuperação do firmware do microcontrolador PIC12F629 ou a restauração do dispositivo é necessária. Essas configurações protegidas, criptografadas ou bloqueadas dificultam a abertura, a descriptografia ou a recuperação de informações úteis do microprocessador PIC12F629 criptografado usando ferramentas padrão. Até mesmo interfaces de depuração avançadas são desabilitadas, deixando poucas opções para aqueles que tentam restaurar ou clonar um microcomputador PIC12F629 bloqueado sem os arquivos originais.
· Watchdog Timer (WDT) with Independent Oscillator for Reliable Operation
· Multiplexed MCLR/Input Pin
· Interrupt-on-Pin Change
· Individual Programmable Weak Pull-ups
· Programmable Code Protection
· High Endurance Flash/EEPROM Cell
– 100,000 write Flash endurance
– 1,000,000 write EEPROM endurance
– Flash/Data EEPROM Retention: > 40 years
Low-Power Features:
· Standby Current:
– 1 nA @ 2.0V, typical
· Operating Current:
– 8.5 mA @ 32 kHz, 2.0V, typical
– 100 mA @ 1 MHz, 2.0V, typical
· Watchdog Timer Current
– 300 nA @ 2.0V, typical
· Timer1 Oscillator Current:
– 4 mA @ 32 kHz, 2.0V, typical
Peripheral Features:
· 6 I/O Pins with Individual Direction Control
· High Current Sink/Source for Direct LED Drive
· Analog Comparator module with:
– One analog comparator
– Programmable on-chip comparator voltage reference (CVREF) module
– Programmable input multiplexing from device inputs
– Comparator output is externally accessible
· Analog-to-Digital Converter module (PIC12F675):
– 10-bit resolution
– Programmable 4-channel input
– Voltage reference input
· Timer0: 8-Bit Timer/Counter with 8-Bit Programmable Prescaler
· Enhanced Timer1:
– 16-bit timer/counter with prescaler
– External Gate Input mode
– Option to use OSC1 and OSC2 in LP mode as Timer1 oscillator, if INTOSC mode selected
· In-Circuit Serial ProgrammingTM (ICSPTM) via two pins
We offer industry-leading services to safely and effectively attack Microchip PIC MCU PIC12F629—not in a malicious sense, but as a means of authorized recovery, duplication, or analysis. Our process involves advanced decapsulation, memory analysis, and proprietary techniques designed to break the fuse protection, unlock the MCU, and recover the embedded firmware without damaging the chip.
Una volta attivato il fusibile di protezione del codice MCU PIC12F629, la memoria di programma interna, la EEPROM e altri archivi di dati diventano inaccessibili tramite i mezzi convenzionali. Questa progettazione garantisce che il codice sorgente proprietario, i file esadecimali e il binario dell’applicazione non possano essere letti, copiati o duplicati senza un accesso appropriato. Protegge la proprietà intellettuale degli sviluppatori, ma introduce anche difficoltà in scenari legittimi in cui è necessario il ripristino del firmware o del dispositivo del microcontrollore PIC12F629. Queste impostazioni protette, crittografate o bloccate rendono difficile aprire, decrittografare o recuperare informazioni utili dal microprocessore PIC12F629 crittografato utilizzando strumenti standard. Persino le interfacce di debug avanzate sono disabilitate, lasciando poche opzioni a coloro che tentano di ripristinare o clonare un microcomputer PIC12F629 bloccato senza i file originali.
Our experts can help you:
-
Dump the full contents of protected memory
-
Replicate the firmware onto new devices
-
Duplicate legacy systems when source files are lost
-
Decode and restore original application behavior
We use highly controlled procedures that avoid triggering auto-erase protections, ensuring the safety of your data. With our extensive experience across Microchip’s MCU families, we deliver success where standard recovery fails.
-
Proven results with locked and secured MCUs
-
Ethical, confidential, and legally compliant service
-
Advanced lab capabilities for chip-level recovery
-
Custom solutions tailored to your project’s needs
एक बार सुरक्षित MCU PIC12F629 कोड सुरक्षा फ़्यूज़ सेट हो जाने के बाद, आंतरिक प्रोग्राम मेमोरी, EEPROM और अन्य डेटा संग्रह पारंपरिक तरीकों से अप्राप्य हो जाते हैं। यह डिज़ाइन सुनिश्चित करता है कि मालिकाना स्रोत कोड, हेक्सिमल फ़ाइलें और एप्लिकेशन बाइनरी को उचित पहुँच के बिना पढ़ा, कॉपी या डुप्लिकेट नहीं किया जा सकता है। यह डेवलपर्स की बौद्धिक संपदा की रक्षा करता है, लेकिन वैध परिदृश्यों में भी मुश्किलें पैदा करता है जहाँ सुरक्षात्मक माइक्रोकंट्रोलर PIC12F629 फ़र्मवेयर रिकवरी या डिवाइस बहाली आवश्यक है। ये संरक्षित, एन्क्रिप्टेड या लॉक की गई सेटिंग्स मानक टूल का उपयोग करके एन्क्रिप्टेड माइक्रोप्रोसेसर PIC12F629 से उपयोगी जानकारी को खोलना, डिक्रिप्ट करना या पुनर्प्राप्त करना मुश्किल बनाती हैं। यहां तक कि उन्नत डिबगिंग इंटरफ़ेस भी अक्षम हैं, जो मूल फ़ाइलों के बिना लॉक किए गए माइक्रोकंप्यूटर PIC12F629 को पुनर्स्थापित या क्लोन करने का प्रयास करने वालों के लिए कुछ विकल्प छोड़ते हैं।

